Server and Agent communication
Published 07 August 2013
When we designed Deployment Manager, we wanted to make it easy to have secure deployments out of the box without expecting machines to be on the same domain. Here's a common use case: your Deployment Manager server is running in your local LAN, close to your developers, and your production servers are running in the cloud or at a remote data center.
We use public-key cryptography to combine secure deployments with the flexibility to deploy anywhere.
Communication between the Agent and the server
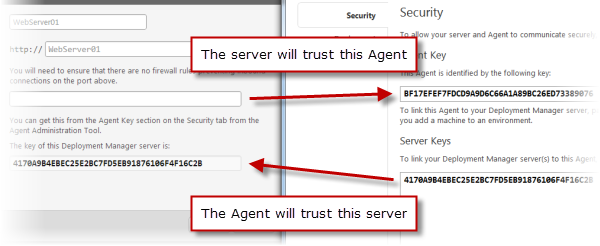
The Agent service listens on a TCP port (by default, 10301). Deployment Manager sends commands to it in the form of HTTP requests encrypted using X.509 certificates. This establishes a trust relationship between the two machines:
- Your Deployment Manager server only issues commands to the Agents that it trusts
- Your Agents only accept commands from a Deployment Manager server they trust
When you install the Agent service, you add a key for the Deployment Manager servers it should trust. When you register a machine in Deployment Manager, you add the Agent key. The image below shows the Deployment Manager web interface where machines are registered, and the Agent administration application:
Since this is all based on public-key cryptography, it creates a highly secure way for the two machines to communicate without exchanging secret passwords, and works much like an SSH connection in UNIX systems. You can further restrict access using IPSec or VPNs, but this usually isn't necessary.
Agent permissions
By default, the Agent service runs as Local System. This is because during deployments the Agent usually needs to perform tasks that require a high-degree of access to the machine. If you want to limit the permissions granted to the Agent, it's better to create a Windows user that has only the permissions you know are required in your process and configure the Agent service to run as that account.
Changing the Agent port
By default, the Agent uses TCP port 10301. To change it, set the value stored in the registry key HKLM\Software\Red Gate\Deployment Manager\Agent.Services.PortNumber to the TCP port you want the Agent to use. For any changes to this value to take effect you'll need to restart the Deployment Agent service in the Windows Services console.
Port forwarding
Port forwarding won't work for the Agent port, because the Microsoft WCF libraries that Deployment Manager relies on for communication between the Agent and the server don't support port forwarding.