Custom Entra ID Authentication Configuration
Published 07 August 2025
SQL Prompt now supports configuring a custom Entra ID application to handle authentication using user-defined settings. This feature allows integration in both commercial Azure environments and national cloud environments such as Azure US Government.
Set up Custom Entra ID Application
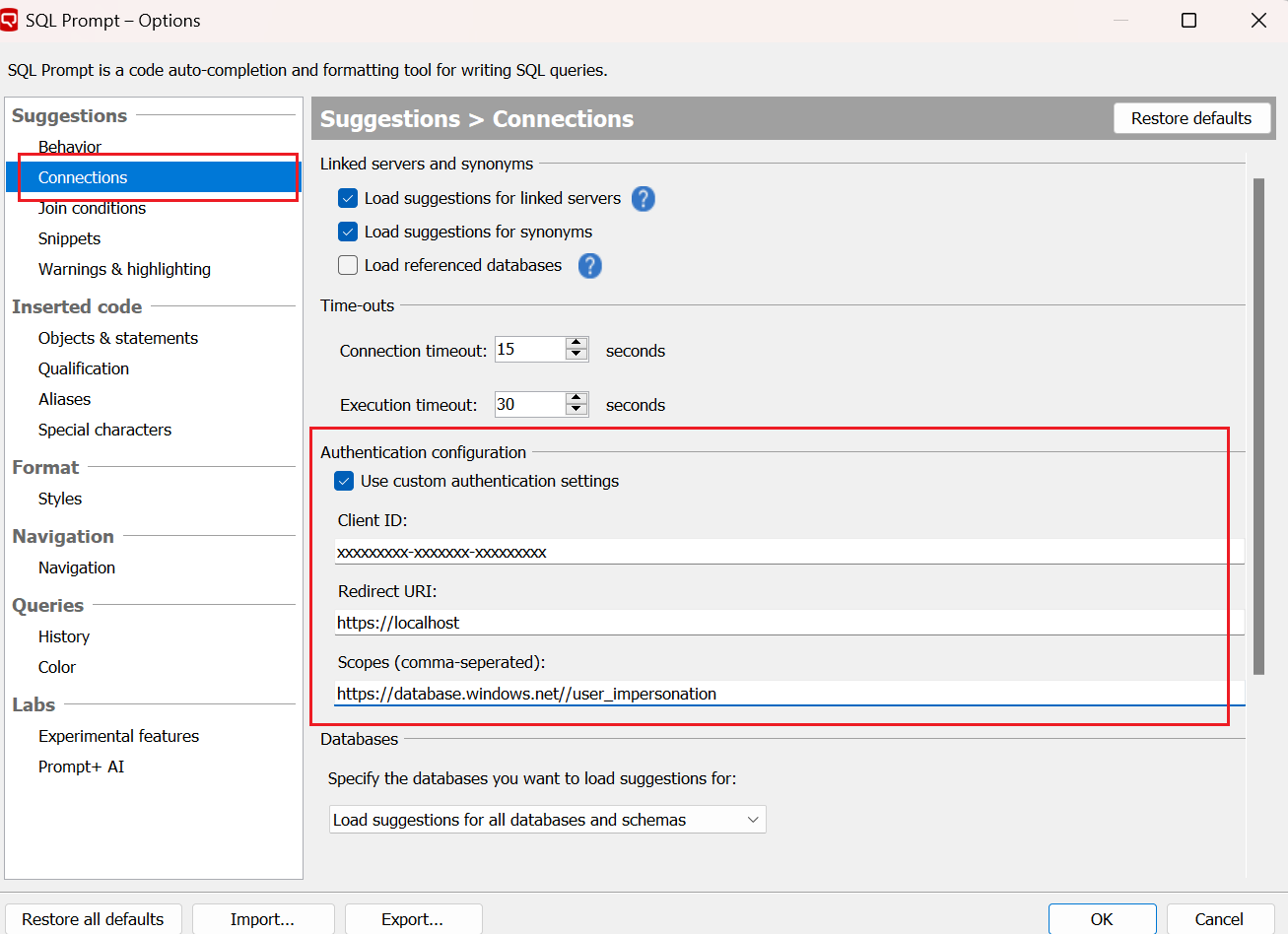
- Navigate to SQL Prompt → Options → Connections → Authentication Configuration
- Enable “Use custom authentication settings”
- Enter the following values:
- Client ID: Your registered application's client ID.
- Redirect URI: The redirect/callback URL registered in your app (e.g., https://localhost)
- Scopes: The required scope(s), e.g., https://database.windows.net//user_impersonation
Ensure your Entra ID application has the necessary API permissions granted and is registered in the appropriate Azure cloud (Commercial or US Gov)
App Configuration Steps
Register an app in Microsoft Entra ID, based on your cloud environment:
- Azure Commercial tenants → Use https://entra.microsoft.com/
- US Government Cloud tenants → Use https://portal.azure.us
- Add a Redirect URI (e.g., https://localhost)
- Under API Permissions, click Add a permission → APIs my organization uses
- Search for Azure SQL Database
- Choose Delegated permissions
- Add the permission: user_impersonation
Locating Required Fields in the Azure Portal
- Client ID → Found in App registrations → Application (client) ID
- Redirect URI → Set in Authentication → Redirect URIs
- Scopes → Configured in API permissions → Add a permission