Editing configuration
Published 07 July 2025
The configuration for Redgate Test Data Manager can be found in the installation path you selected.
The file is called config.yml.
We highly recommend using any text editor with the ability to highlight syntax to detect any mistake during the editing of the configuration file.
Editing any value in this configuration file requires a restart of the Redgate TDM Service (TDMService).
If any of the fields that were mentioned in this page do not exist in your configuration file, you can add it in yourself.
The following items are things you can edit:
Initial Setup
These fields configure the settings normally completed through the Setup Wizard. Use these if you want to avoid the setup wizard or need to modify settings after completing the wizard.
Config.yml fields
Add the following fields to your config.yml:
EulaAcceptedLicensingEmailLicensingPatUnsafeDemoPassword
Environment variables
Alternatively, configure these settings through environment variables:
REDGATE_TDM_EULA_ACCEPTEDREDGATE_LICENSING_PAT_EMAILREDGATE_LICENSING_PAT_TOKENREDGATE_TDM_UNSAFE_DEMO_PASSWORD
Network configuration
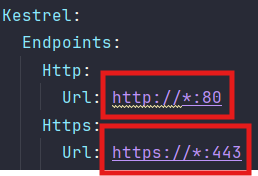
These configurations are under the Endpoints section under Kestrel section.
Application port number
The application needs two ports to work properly—one for regular connections (HTTP) and one for secure connections (HTTPS).
Even though the regular connection (HTTP) is needed for setup, people using the app will always be redirected to the secure version (HTTPS) automatically.
If you want to change the port numbers, just update the number after the semicolon in each section.
The regular (HTTP) port is only there to help redirect users to the secure one.
The secure (HTTPS) port is the main one used to run the app.
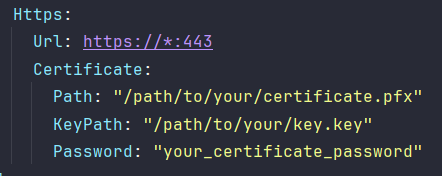
SSL certificate
By default, the installer will generate a self-signed SSL certificate to use for HTTPS.
If you want to use other certificates, you can do this by editing this section.
There are three fields used to configure your SSL certificate:
Path(required) – Specifies the path to your certificate file (e.g.,.pfx,.crt, or.pem).KeyPath(optional) – Specifies the path to the private key file, if it's stored separately from the certificate.Password(optional) – Specifies the password used to access the certificate or decrypt the private key, if applicable.
We don't recommend using a certificate without any type of encryption, as it is considered not safe.
Ensure your certificate's Subject Name or Subject Alternate Name matches the hostname users will use to access Test Data Manager.
Do not have both KeyPath and Password fields present in the configuration file because it will cause an error and the service will not able to run.
Application database connection
If you have a new database connection string you want to replace, you can simply replace it in the ConnectionString field under the TDM section.
Authentication method
Basic authentication
- By default, Redgate Test Data Manager will use this authentication method.
- Changing password can be done by editing
UnsafeDemoPassword.
For safety reasons, we do not allow user to enable basic authentication if you already had use OIDC method at least once.
OIDC
To switch to using OIDC, you can simply do it by filling the following fields:
AuthAuthority- The URL of your Identity Provider's authorization server
- Example https://identityprovider.example.com
AuthScope- The application scope you configured for Test Data Manager in your Identity Provider.
- Example:
TDM.Solution
AuthAudience- The valid audience you configured for Test Data Manager in your Identity Provider.
- Example:
TDM.Solution.Web.Api
AuthClientId- Test Data Manager's application client ID as configured in your Identity Provider.
- Example:
12345678-1234-1234-1234-123456789012
Make sure that UnsafeDemoPassword field does not have any value in it before enabling OIDC.
Optional fields
AuthIssuer- The URL of your Identity Provider's issuer.
- This only needs to be set if it differs from
AuthAuthority. - Example: https://issuer.identityprovider.example.com
AuthUserNameClaimType- The claim type that identifies the user in your Identity Provider.
- By default, we use email claim type, however some Identity Providers may use a different claim type to identify the user.
- Example:
preferred_username
AuthAdminRoleClaim- The claim type that identifies if the user is an Admin.
- This is needs to set to 'rgtdm_admin' as RGClone identifies Admins by this claim type.
- Example:
rgtdm_admin