Preparing for adding monitored servers
Published 21 October 2021
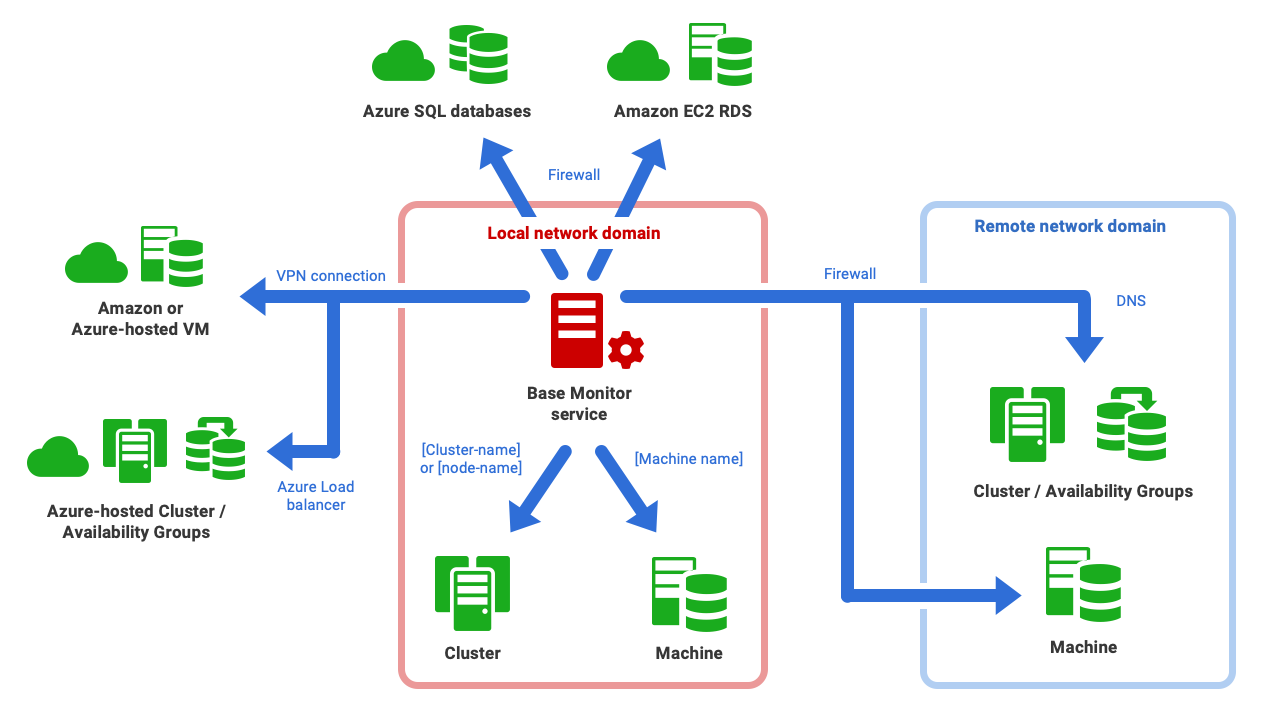
If you're adding an instance running on a local network machine, little preparation is required beyond ensuring that the login account you supply has sufficient permissions to collect the required monitoring data. However, if the Base Monitor must monitor servers on remote domains, with firewalls involved, it's worth sitting down your sysadmin to discuss the requirements and considerations beforehand.
This page provides a "preparation checklist" for adding monitored machines and SQL Server instances, with links to pages that provide the required details, depending on your requirements:
WMI Connections: WinRM or DCOM?
When automation became key to DevOps processes, PowerShell with "remoting" over WinRM became the obvious way of maintaining and servicing the separate components of a busy and changing IT infrastructure, especially when used with WMI. It is a standard SOAP-based (Simple Object Access Protocol), firewall-friendly protocol that allows hardware and operating systems, from different vendors, to interoperate. Your server estate is best accessed via WinRM so it is worth aiming for this.
- If using WMI over DCOM, go to: WMI over DCOM.
- If using WMI over WinRM, go to: WMI over WinRM.
- If the Base Monitor must make connections to servers in a different network domain, and so navigate firewalls, review Adding servers on a different network from your Base Monitor and Summary of firewall requirements, .
Adding SQL Server instances running on different types of server
Resolving connection issues
For security reasons, SQL Monitor monitors SQL Server machines and instances without requiring an "Agent" to be installed on each machine. However, this does mean SQL Monitor can be more sensitive to the network setup than an agent-driven monitoring system (which can provide pre-packaged troubleshooting routines). If you're monitoring instances on a local network, with SQL Server hosted within a Windows Domain, you'll have no difficulties, of course. Likewise, where network monitoring is already automated with remote scripting, there are few if any issues. Where the WS-Management protocol is already used in a domain or heterogeneous network, you are unlikely to hit problems.
However, if you hit problems connecting to a remote server or instance, we suggest the following:
- Go to Configuration > Monitored Servers, in the web interface, and check the monitoring status, for machine and instance, and the SQL Monitor logs for the possible source of the problem.
- Interrogate via WMI each of the machines to which you wish to connect and monitor, using the command line, SSMS or PowerShell.
See: What to try if you hit connection problems.
Permissions required to monitor servers and instances
For each remote server that you wish to monitor, you need to provide the Base Monitor service with a login account to connect to it, and with:
- Sufficient permissions on the remote machine to collect the monitoring data.
- Login rights on the machine hosting the Base Monitor service, since SQL Monitor must be able to authenticate the account locally.
Similarly, you'll need to supply a login account that the Base Monitor service can use to monitor each SQL Server instance.
The Base Monitor service will need to collect detailed diagnostic data from the Windows machine and from each of the monitored SQL Server instances. As such, ideally, the Base Monitor service will either run as a domain account that is both of the following, or will have access to other accounts that are:
- A member of the Windows administrator group on the remote machine.
- If this is not possible, see Monitoring host Windows machines without admin permissions.
A member of the sysadmin fixed server role, on the SQL Server instance.
If this is not possible:
Authenticating using domain accounts
- By default, SQL Monitor will use the Windows/Active Directory domain account that is running the Base Monitor service to connect both to the Windows machine and the SQL Server instances it hosts. SQL Monitor supports use of a group managed service account (gMSA).
- However, you can also supply the Base Monitor service with one or more separate accounts to collect the Windows and SQL Server data.
- You add the user account to SQL Monitor on the Configuration > Monitored servers page, and a domain user is entered with the domain qualifier. You can specify:
- A Windows / Active Directory login on the monitored server to collect data from Windows.
- Either a Windows / Active Directory account or a SQL Server login to collect data from SQL Server.
- You add the user account to SQL Monitor on the Configuration > Monitored servers page, and a domain user is entered with the domain qualifier. You can specify:
- If you are using an AD-authenticated account to connect between domains, you may need to ensure that there is bi-directional trust between them.
Authenticating using non-domain accounts
To connect to remote machines, SQL Monitor must authenticate the user locally, to the machine where the Base Monitor is installed. Therefore, with non-domain user accounts, you need to have on each machine (the Base Monitor machine and the remote machine) the same local user with the same password (i.e. UserName1 with Password1 must exist on both machines).
- Add the user to SQL Monitor on the Configuration > Monitored servers page as .\UserName1 so that it will use the user local to each machine. This will be automatically changed to display as UserName1@, but don't worry about this.
- You may also need to add the registry key specified in this article to stop the UAC from reducing the user's privilege when accessing the machine remotely (this is on the machine you want to monitor).