Proposed SSH Key authentication usage
Published 11 July 2023
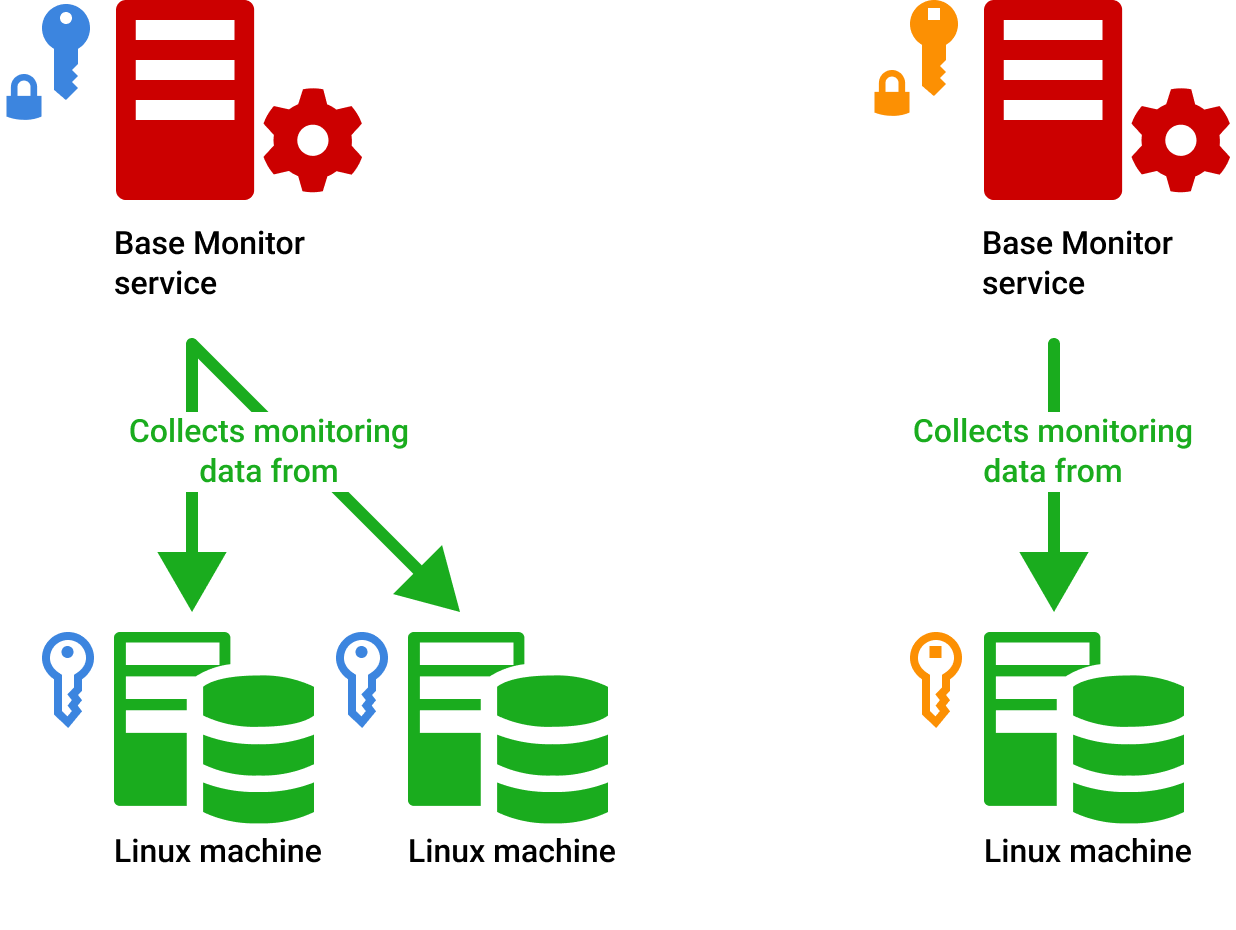
We recommend generating and assigning a single SSH private key per BM, as seen in the following diagram.
The public part of the key can then be added to the Linux machines monitored by that particular BM.
The proposed usage is in accordance with how the BM service accounts should be used.
For example, if two BMs run under the same Windows account for scale or latency reasons, then the same SSH key can be used as well.
If two BMs run in separate security domains, then we recommend having separate keys.
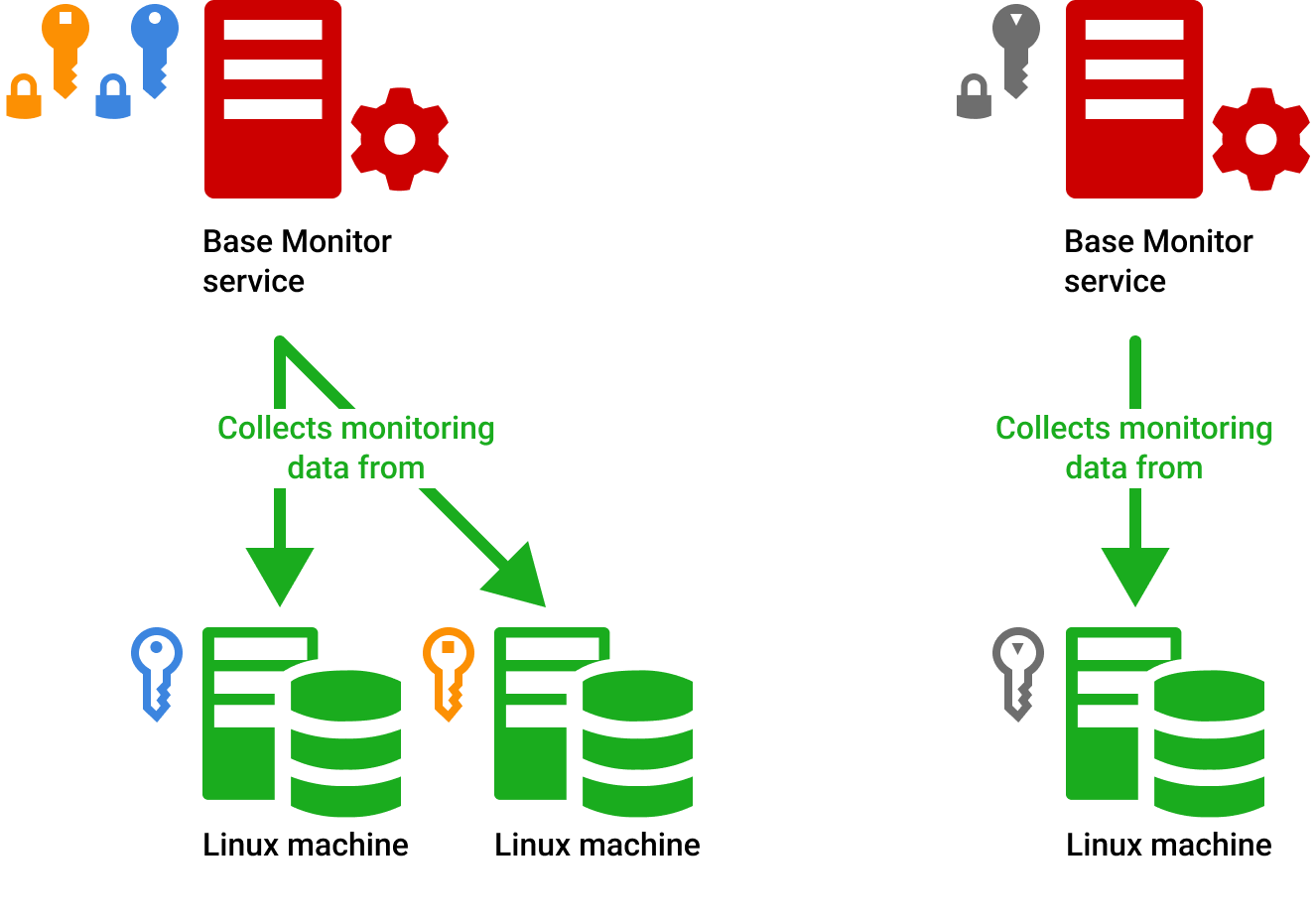
The main advantage of this approach is that it reduces the risk of compromise. If the BM host is compromised, only a single encrypted private key is at risk. This is because each BM uses its own unique private key. Therefore, if one BM is compromised, the rest will not be affected.
This approach improves security by:
- Reducing the number of SSH private keys that need to be protected per BM.
- Making it more difficult for an attacker to compromise all of the SSH private keys at once.
Having more than one unique private keys per BM is also possible, depending on your use case