Permissions required for the SQL Monitor Service accounts
Published 17 August 2020
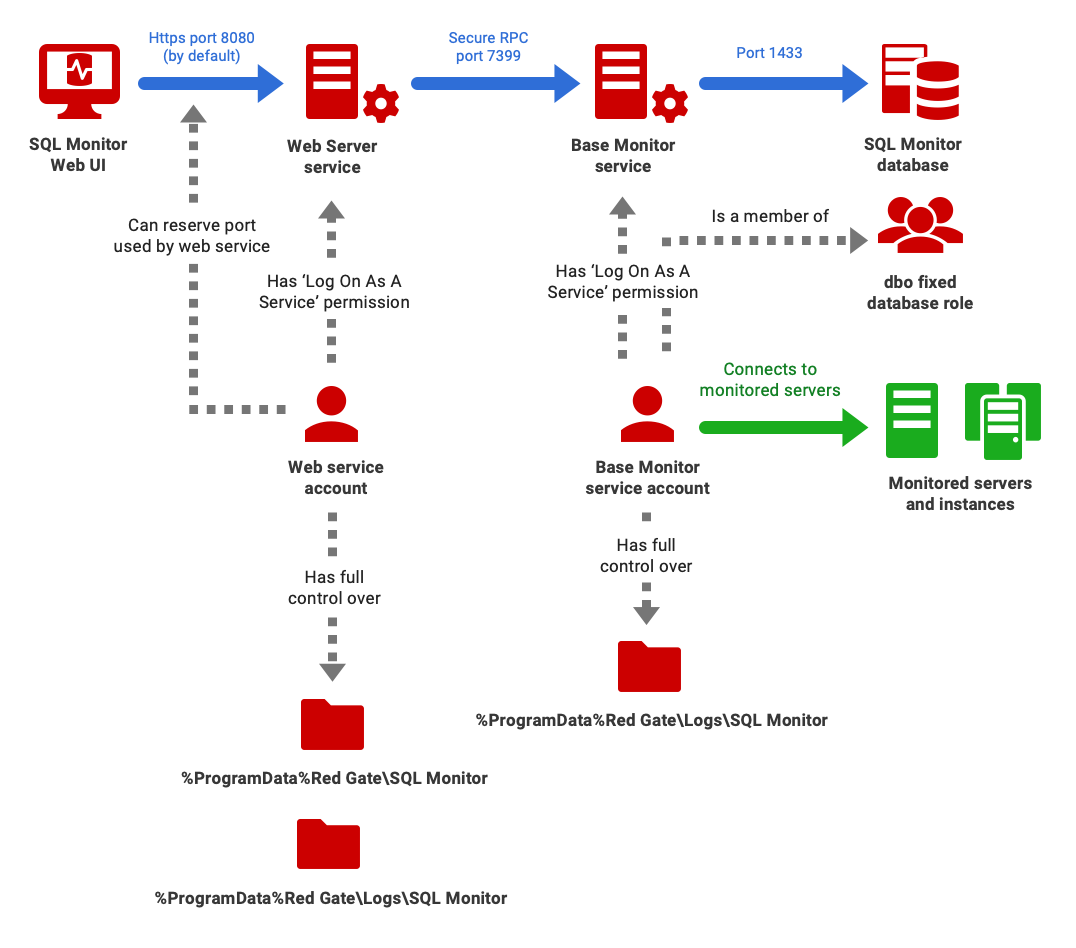
The following diagram depicts a 3-server installation of SQL Monitor, shows the connections between the major SQL Monitor components (red arrows), and summarizes the permissions required for the Base Monitor and Web Server Services accounts. The Base Monitor service will also need to connect to the servers and instances that it needs to monitor; this can use the Base Monitor service account or other accounts.
The Service account details are established initially as part of the SQL Monitor installation process, but you can change the account used to run either service via the Log On tab of the Properties screen for that service.
Web Service account requirements
The Web Server Service account requires the following permissions:
- The account should have Log on as service rights. For information on how to assign these permissions, see Add the Log on as a service right to an account.
- The account should have Full Control over the folder
%ProgramData%\Red Gate\SQL Monitor. For versions of Windows prior to Windows Server 2008R2:C:\Documents and Settings\All Users\Application Data\Red Gate\SQL Monitor. - The account should have Full Control over the folder
%ProgramData%\Red Gate\Logs\SQL Monitor.This will usually resolve to ‘
C:\Documents and Settings\All Users\Application Data\Red Gate\Logs\SQL Monitor’, although on older installations it was usually ‘C:\ProgramData\Red Gate\Logs\SQL Monitor‘.
The account should be able to reserve the port that the web service is configured to use. To do this, run in an admin command console on the server:
netsh http add urlacl url=http://*:<SQMport>/ user=<my WebServiceAccount >
where<SQMport>is the port you are using to access SQL Monitor (it uses port 8080 by default, but you may well wish to change this), and<WebServiceAccount>is the name of the Web Service Account.
If you install the default SQL Monitor Web Server, then after initial installation the Web Service account will be running as a Local system account (the LocalService account) to which SQL Monitor will have granted the required permissions on the local machine, during installation. However, you can subsequently configure it to use a different account:
Any alternative account will need the previously listed permissions, either by its group membership or explicitly. If the account has membership of the local administrators’ (sysadmin) group then it will have the permissions by default. However, you may want to avoid this for security reasons, and all required permissions are relatively straightforward to establish.
Base Monitor Service account requirements
The Base Monitor Service requires access to one or more accounts to:
Run the service on the local machine
This is the Base Monitor Service account, and it requires the following permissions:
- The account should have Log on as service rights. For information on how to assign these permissions, see Add the Log on as a service right to an account.
- The account should have Full Control over the folder
%ProgramData%\Red Gate\Logs\SQL Monitor.- This will usually resolve to ‘
C:\Documents and Settings\All Users\Application Data\Red Gate\Logs\SQL Monitor’, although on older installations it was usually ‘C:\ProgramData\Red Gate\Logs\SQL Monitor‘.
- This will usually resolve to ‘
Connect to the SQL Monitor database
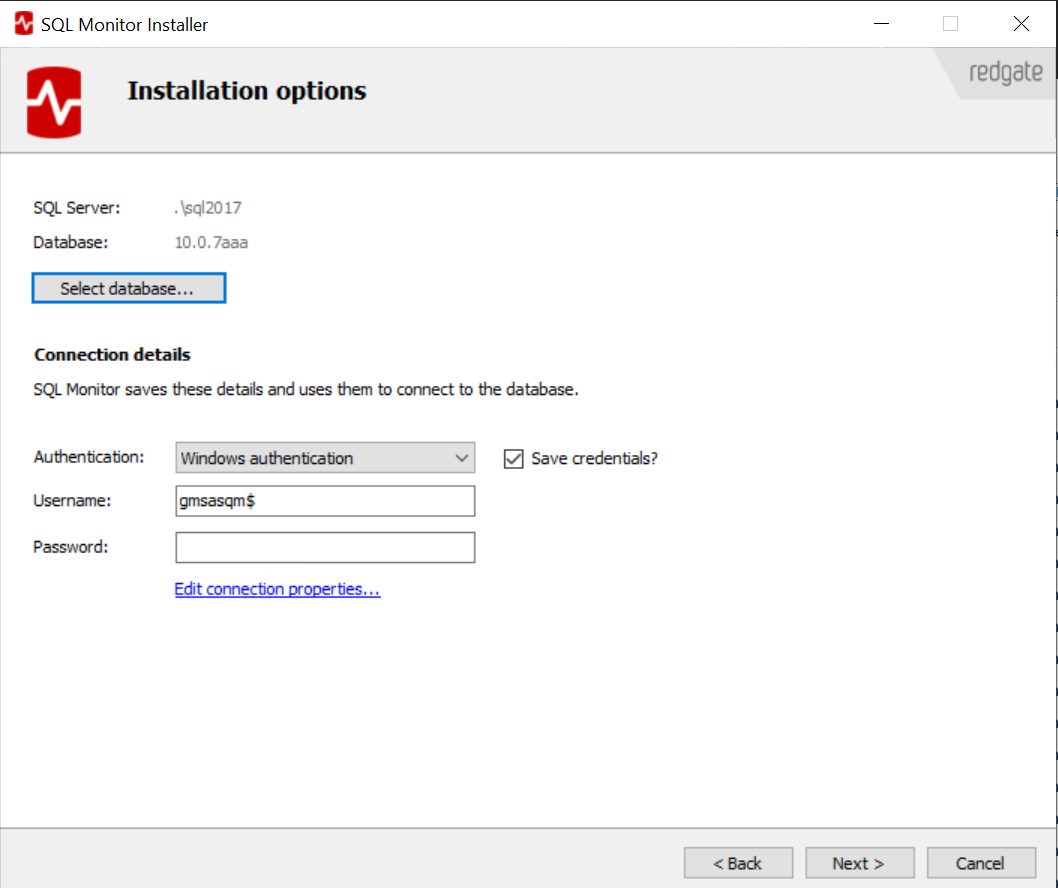
The account that the Base Monitor service uses to access the data repository is specified in the Connection Details section of the installer. It can be either the Windows service account or a SQL login account.
- The account should be a member of the db_owner database role on the Data Repository database (called RedGateMonitor by default). This will be granted automatically if you create the Data Repository through the installer.
- If the data repository is hosted on Azure SQL Database, then a user should be created on the master database for the login you are trying to use in the installer.
If you choose SQL Server authentication, then the Base Monitor service will run as a Local system account (the LocalService account) to which SQL Monitor will have granted the required permissions (see above) during installation.
If you choose Windows authentication, with a Windows / Active Directory domain account, then this account will also be used to run the Base Monitor service and it will need the required permissions to do this (outlined above).
Connect to remote servers that you wish to monitor
If you specify a Windows / Active Directory domain account to run the Base Monitor service, this account can be used to grant access to monitored servers; see: Adding servers for monitoring. This can simplify the management of passwords when adding servers. However, you can also supply one or more separate accounts for these purposes.
In any case, the Base Monitor service will need access to one or more accounts with adequate permissions required for monitoring servers.
Group Managed Service Accounts
SQL Monitor supports the use of a group Managed Service Account (gMSA) for the Base Monitor service. If you use a gMSA account to run the Base Monitor, the gMSA can be used to give SQL Monitor access to monitor servers. To specify a gMSA during installation, simply enter the gMSA name with a dollar-mark ($) on the Installation options page: